A Computer Science and Engineering Student Specializing in Cybersecurity. Learn More →
Recent Blog Posts
About

I am a student at Ohio State University studying Computer Science and Engineering, with a minor in Information Security. In addition to my classwork, I have been learning core facets of cybersecurity, with the goal to pursue a forensics role.
Certifications
Certifiably Amazing.





Projects
Knowledge Applied.
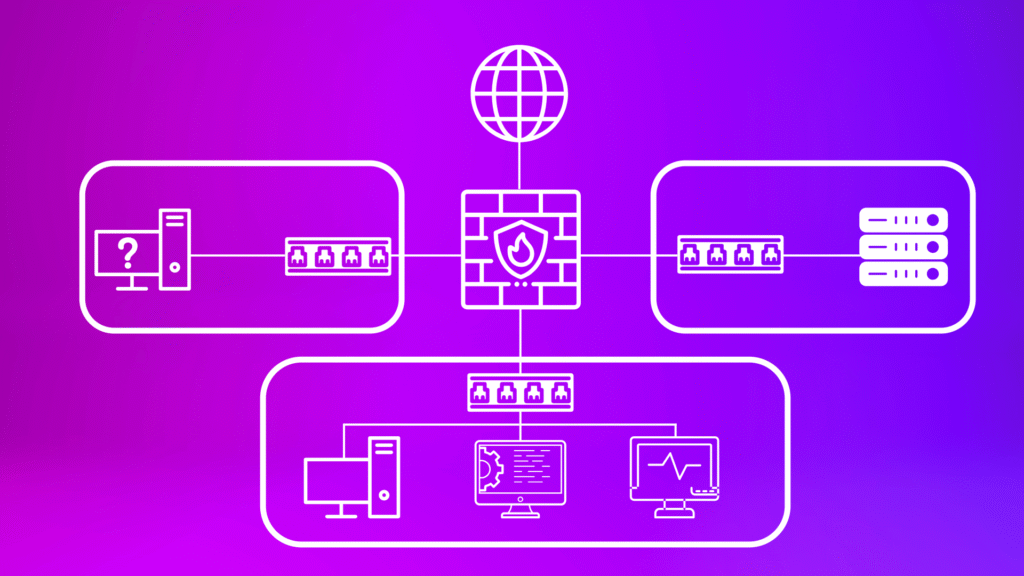
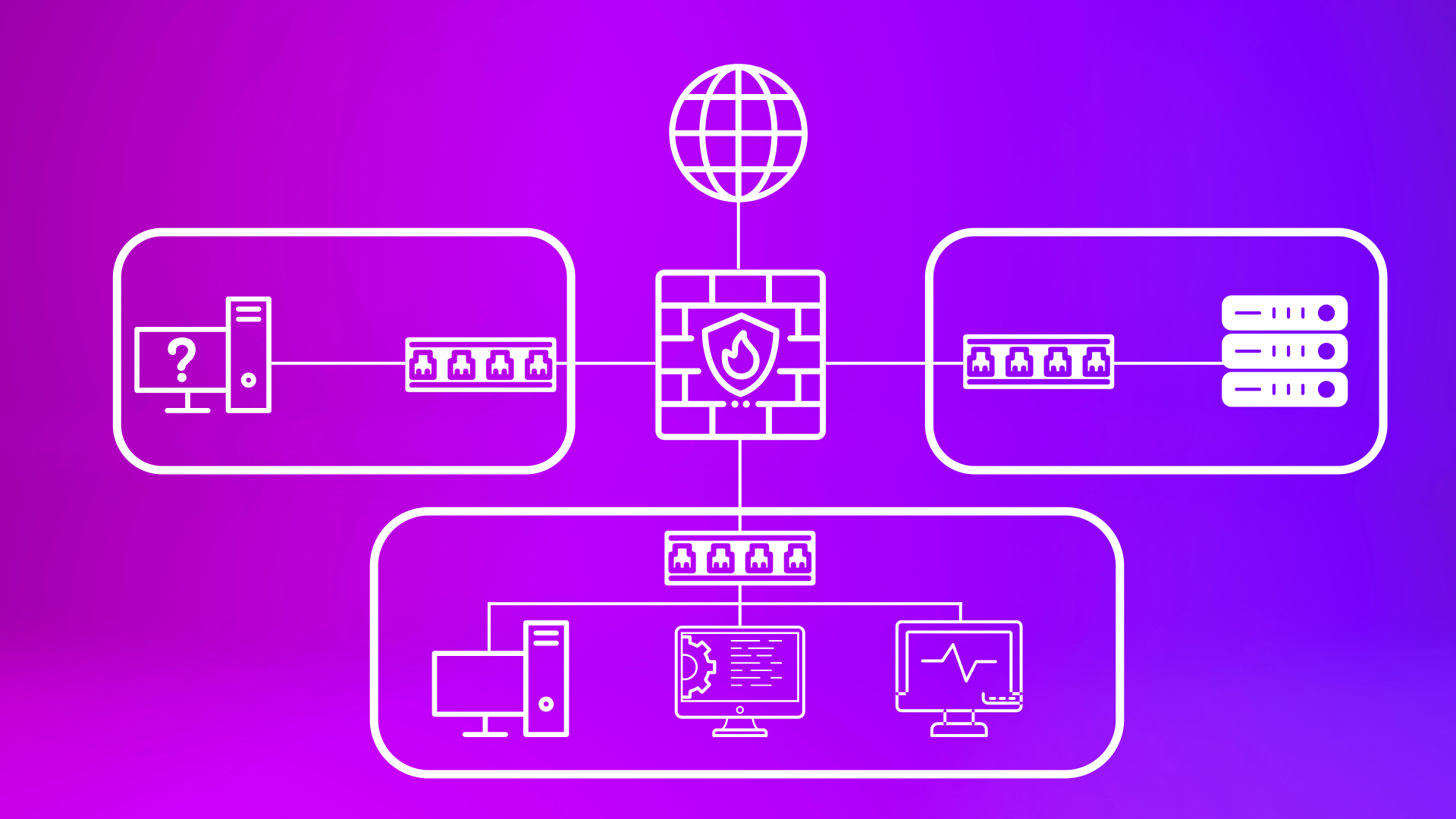
Homelab
I created a simulated office network environment to build a comprehensive security posture, and to test these security measures. Throughout this series, I implement security tools and then perform a penetration test to identify lingering weaknesses. Currently I have implemented Wazuh to act as a SIEM and XDR solution, and pfSense to act as a firewall and router between multiple virtual networks within my virtual environment.

Virtual Penetration Testing Lab
Leveraging VirtualBox, I created a completely isolated virtual network within my the bounds of my computer to attack vulnerable virtual machines.

Remote Start IoT Device
I used an ESP8266 micro controller connected to Adafruit IO to remotely turn on my computer from anywhere in the world. Additionally, I also created a status indicator on my Adafruit IO dashboard that allows me to see the status of my computer at any time.
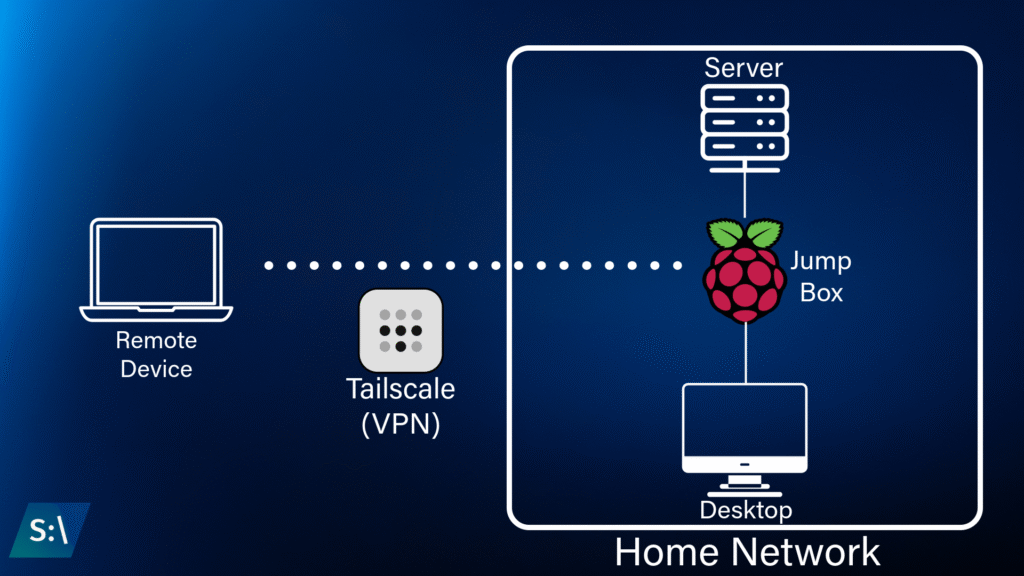
Remote Network Access
I configured a Raspberry Pi to act as a jump box to my home network, using Tailscale to create a secure VPN tunnel over the open internet. This jump box was used to wake other machines from sleep on my network, and acted as a pivot point to facilitate terminal and remote desktop access to other machines on my network.
Competition Appearances
Skills Tested.

SAE AutoDrive Challenge II Year 4 Competition
The AutoDrive Challenge requires teams to create an autonomous vehicle that is able to successfully navigate a course with no driver intervention in accordance with Level 4 Autonomy in the SAE Levels of Autonomy. In this competition, I presented about various year-to-year improvements along with our new Human Machine interface (HMI) at the Concept Design Event. Additionally, I also assisted in testing and ensuring our vehicle was ready to compete.

BuckeyeCTF
Competed in 2022, 2023, and 2024 (9th Place – Undergraduate Division)
Hosted by the Cybersecurity Club at Ohio State, this is a capture the flag competition where I had to solve as many cybersecurity challenges in 48 hours. During these events, I primarily solved forensics and web challenges.

Buckeye Programming Competition 2024
Hosted by the Competitive Programming Club at Ohio State, this was a competition where I had a weekend to solve a series of programming challenges.
Professional Experience

IT Helpdesk Assistant
The Ohio State University Department of Athletics
September 2023 – Present
• Configured Qualys Web Application Scanning (WAS) to manage vulnerabilities on web applications in order to remain compliant with university information security policies
• Wrote a library of Powershell scripts to automate the setup process for new computers in many possible deployment scenarios
• Remediate vulnerabilities and respond to Crowdstrike EDR detection alerts
• Assist coaches and support staff with IT needs such as troubleshooting computer issues and configuring mobile devices, troubleshoot network configurations
• Prepare old hardware for surplus and update inventory
• Assist with IT support for Athletic department hosted events

Vehicle Integration Developer
Buckeye AutoDrive
August 2024 – Present
• Presented at the SAE AutoDrive Challenge II Year 4 Competition Concept Design Event
• Perform offensive cyber security research using decompilation and packet capture tools
• Develop a custom Human-Machine Interface (HMI) to enhance driver interaction with vehicle systems in both autonomous and manual modes
• Interpret communication data on CAN bus subsystems for vehicle diagnostics and operations
• Collaborate with the Vehicle Integration Department to create reliable systems ensuring safe vehicle operation in autonomous driving environments
Lead Welcome Sites Attendant
New Albany Country Club
September 2020 – August 2023
Awarded Employee Spotlight Award – April 2022
• Created training manual for Welcome Sites Operation
• Oversee Welcome Sites staff and ensure quality of work
• Create schedule for the Welcome Sites team, maintain rental locker system and monthly usage reports, train new staff members
• Assist with the daily operation of the Bath and Tennis facility
• Welcome members and assist with any general needs during visit, assist members over the phone
• Charge retail purchases in addition to tennis clinics and member events
Skills










Academics

Ohio State University
Bachelor of Science – Computer Science and Engineering
Software Engineering Specialization
Information Security Minor
Dean’s List: Fall 2021, Spring 2022, Spring 2024, Spring 2025
Extracurricular Activities: Athletic Band, Cybersecurity Club, Competitive Programming Club
August 2021 – December 2025

Ohio State University – Newark
Associate of Arts
August 2021 – May 2024